A complicated model of crypto-mining malware has been discovered recently that may very well be a severe risk to Huawei Cloud and customers. This malware was beforehand reported attacking the open-source software program growth platform- Docker Containers.
As per the report, this new malware model has sufficient algorithms to dodge the firewall guidelines creation operate. Including to this, it leaves a community scanner behind to trace API-relevant ports of the opposite hosts.
Nonetheless, this new crypto-mining malware is presently energetic in cloud environments. Moreover, it’s checking for the opposite ecosystem that has beforehand been affected by this assault.
Earlier than discussing its different particulars, let’s first know what crypto-mining is-
What’s Crypto-mining :
Crypto-mining or Cryptojacking is outlined as an internet thread or malware that holds the power to hamper and even crash a company’s digital atmosphere. As well as, it labored whereas staying utterly hidden from a person.
In Cryptojacking, the attacker can use the sufferer’s units with out their considerations to secretly mine cryptocurrency. Likewise, it additionally causes monetary losses for the sufferer and disruption to enterprise workings. Furthermore, it primarily targets cryptocurrencies or digital cash.
On a Linux system, this digital forex miner malware has to comply with a process proven within the determine. It not solely harms the system however concurrently removes its traces.
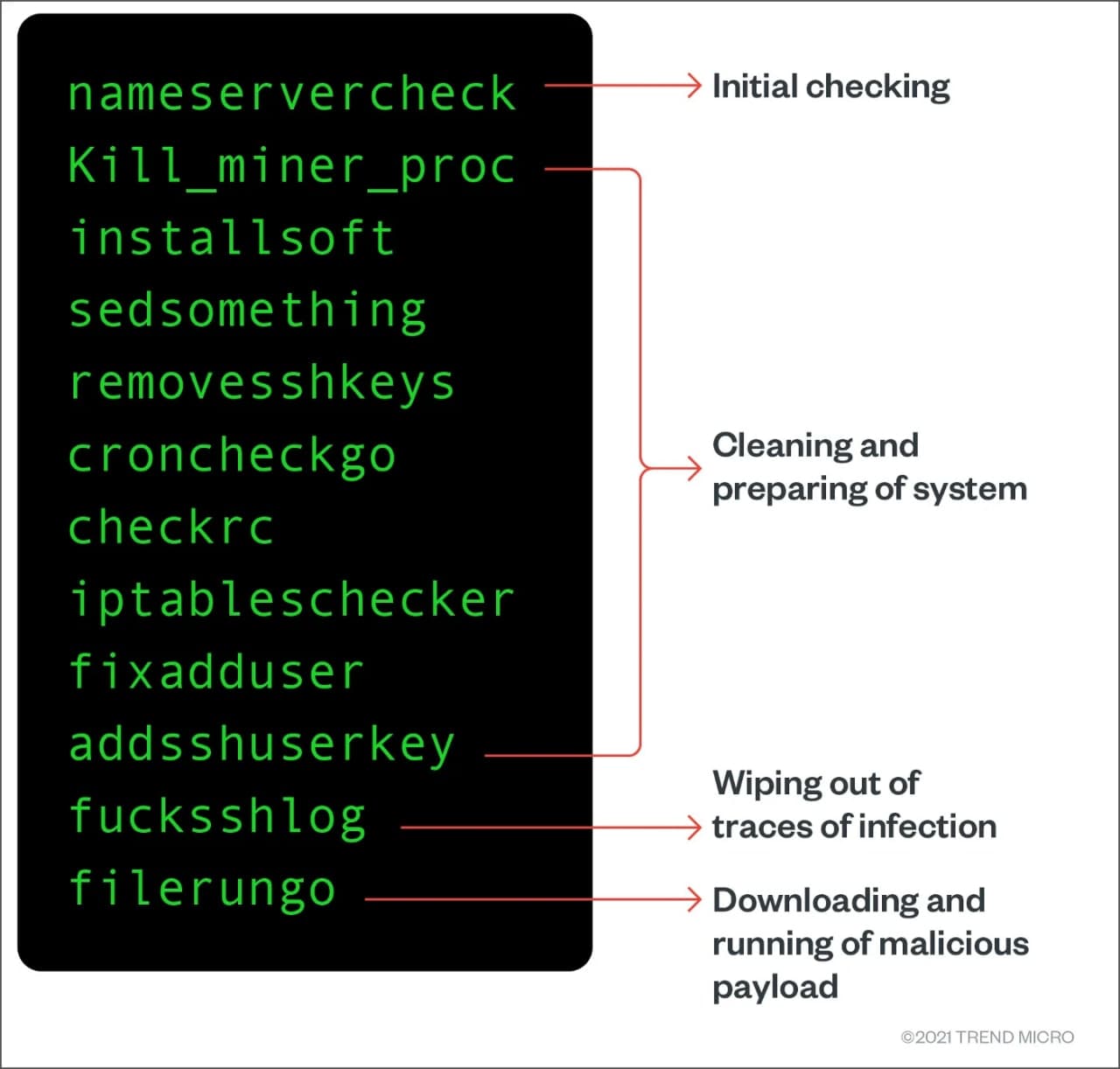
Afterward, it replaces all customers added by the opposite actors with the one created by them. It’s one of many fundamental steps follows by the cloud-targeting cryptojackers. In contrast to different attackers, the cryptojackers use the Sudo applications of their accounts that present root entry to the system.
Moreover, the attacker makes use of their very own sh-RSA key to carry out system changes and alter the file permissions to a locked state. It restricts different customers to get complete management of the susceptible pc or machine even when they acquire entry to the machine.
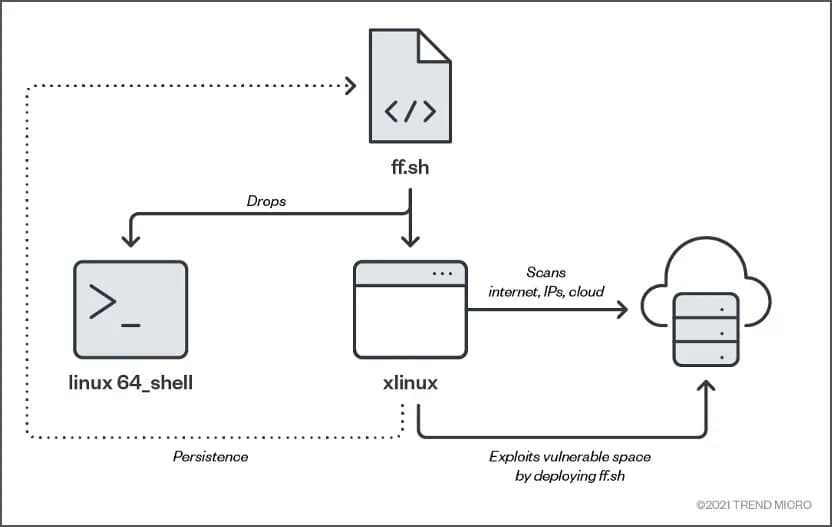
In addition to, the actors set up the Tor proxy service that helps them in stopping from establishing a connection to different community scanning detection. For wrapping, there are binaries codes (linux64_shell, ff.sh, fczyo, xlinux) at UPX packer. As soon as the assault get full management of the machine, it started to execute its malicious actions.

Nonetheless, there are some identified vulnerabilities detected throughout the scan on this assault. Most of them are associated to the weak password in some capabilities that features
Some Identified Vulnerabilities:
- SSH weak passwords
- Vulnerability within the Oracle WebLogic Server product of Oracle Fusion
- Middleware (CVE-2020-14882)
- Redis unauthorized entry or weak passwords
- PostgreSQL unauthorized entry or weak password
- SQLServer weak password
- MongoDB unauthorized entry or weak password
- File switch protocol (FTP) weak password
As you may see, what customers can if on Huawei Cloud if this coin-mining malware has been surfed in precise. To be point out, all of the describe information got here from the main knowledge safety and cybersecurity resolution supplier TrendMicro.
Based on this agency, it has despatched the acknowledgment report back to Huawei Cloud to make the authorities conscious of the crypto-mining malware. Now, we’re ready for Huawei to formally deal with this downside.
(By way of- BleepingComputer)

![Huawei Watch GT 2 update 11.0.14.90 brings bug on some models [CN]](https://nutritioncenter.extremefatloss.org/wp-content/uploads/2021/12/Watch-gt-2-bud-1000x576-750x432.jpg)















